VPN for Secure Online Transactions: Stay Safe
VPNs and Their Importance in Online Security – In an era where online transactions have become a cornerstone of daily activities, the necessity for robust security measures such as Virtual Private Networks (VPNs) has never been more crucial. VPNs create encrypted tunnels that safeguard sensitive information, allowing users to browse the internet securely while protecting against potential cyber threats. This technology not only enhances privacy by hiding users’ IP addresses but also provides a secure connection over public networks, which are often vulnerable to hacking and data breaches. The concept of VPNs is further illustrated by the technical diagram that depicts their operational framework, showing how encrypted connections function between different network points . Understanding the fundamental role of VPNs in shielding personal data is essential for anyone engaging in online transactions, reaffirming their importance as a primary defense mechanism in the landscape of digital security.
II. How VPNs Work to Protect Online Transactions
To effectively safeguard online transactions, Virtual Private Networks (VPNs) utilize advanced encryption protocols, creating secure tunnels for data. This process ensures that sensitive information, such as credit card details or personal identification, remains confidential and protected from potential threats, such as data interception or hacking attempts. By masking the user’s IP address, VPNs further enhance privacy, making it more difficult for adversaries to trace online activities back to an individual. The significance of this protection becomes increasingly relevant as internet privacy concerns mount alongside the growth of data-driven business models, where personal data monetization is commonplace (Marchewka et al.), (Elvy et al.). In conjunction with these measures, diagrams like visually illustrate the functioning of VPNs, presenting a clear understanding of how encrypted tunnels maintain transactional integrity in a world fraught with cyber threats. Thus, VPNs play a critical role in fortifying the security of online transactions.
III. Benefits of Using a VPN for Secure Online Transactions
The utilization of a Virtual Private Network (VPN) is crucial for securing online transactions, particularly in an era where cyber threats are increasingly sophisticated. By encrypting user data, a VPN protects sensitive financial information from eavesdroppers and hackers, ensuring that details such as credit card numbers and passwords remain confidential. Furthermore, as highlighted in research regarding user experience and privacy protection, the way individuals perceive security significantly impacts their interaction with online services (Busse et al.). This perception is further nurtured by the anonymity a VPN provides, allowing users to mask their IP addresses and geographical locations, thereby reducing the risk of targeted cyberattacks associated with identifiable user profiles. Moreover, the benefits of employing a VPN extend beyond abstract security notions; they manifest in concrete practices that can thwart unauthorized access, making secure transactions more reliable and trustworthy, as illustrated in the comprehensive overview of digital security measures .
The image illustrates a conceptual representation of global digital security, featuring a stylized globe interconnected with various devices, including mobile phones and computers. In the center, a shield with a padlock symbolizes protection and cybersecurity, suggesting a networked environment. The background consists of binary code, emphasizing the digital aspect of the subject. This visualization can be utilized to discuss themes related to cybersecurity, the importance of data protection in a globalized digital landscape, and the interconnected nature of technology in modern society.
Image1 : Global Digital Security and Cyber Protection
IV. Potential Limitations and Considerations When Using a VPN
While Virtual Private Networks (VPNs) can enhance security during online transactions, they come with inherent limitations that users must consider. One significant drawback is the potential for reduced internet speeds due to encryption processes, which may lead to frustrating experiences when completing time-sensitive transactions. Moreover, not all VPN services provide equal levels of security; some may use outdated encryption protocols or could even track user data themselves, questioning their reliability as a secure intermediary. A study highlights that users frequently utilize public Wi-Fi, which can inadvertently lead to security breaches despite VPN usage, emphasizing the importance of robust security measures beyond VPNs alone (Sombatruang et al.). This reality reflects a broader issue where complexities in hybrid systems can expose users to additional security threats, as articulated in discussions surrounding IoT and vehicle connectivity (Bilbao-Arechabala et al.). In light of these factors, users must critically evaluate their VPN choice and remain vigilant about broader cybersecurity practices. effectively illustrates the functioning of VPNs, underscoring their role yet also suggesting that understanding their limitations is crucial for ensuring secure online transactions.
The image provides a visual representation of how a Virtual Private Network (VPN) operates. It illustrates the process of connecting two networks or remote clients to central networks using the internet as a transport mechanism. The diagram highlights the creation of an encrypted tunnel between two endpoints, ensuring privacy by obscuring internet traffic. The central cloud area labeled ‘Internet or public infrastructure’ signifies the public network through which the encrypted tunnels are established. This image serves to explain the technical concept of VPNs in cybersecurity.
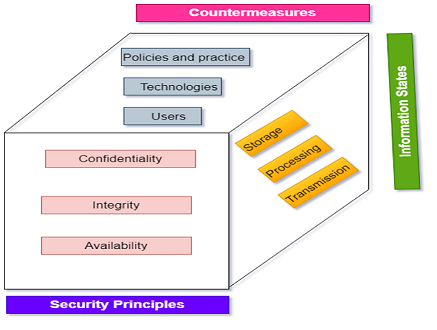
The implementation of Virtual Private Networks (VPNs) is vital for ensuring safe online transactions in an increasingly complex digital landscape. The risks associated with unprotected internet usage, such as data breaches and identity theft, highlight the need for robust security measures. By creating an encrypted tunnel for data transmission, VPNs effectively shield sensitive information from potential threats. Furthermore, the vital role of cybersecurity practices, as depicted in the image showcasing information security principles and countermeasures , underscores the necessity of integrating VPN technology within a comprehensive security strategy. As consumers and businesses navigate the digital world, prioritizing VPN use can significantly mitigate risks, ensuring safe financial transactions and the protection of personal information. Ultimately, embracing such technologies not only enhances security but also fosters greater confidence in digital transactions, paving the way for a secure online environment.